Practice is the only way to check what we know and what we need to know.
In this domain, It is illegal to perform any kind of attack on the running network without proper permission. So, To improve knowledge a lab is created with vulnerabilities that can be exploited by individuals. This lab can be hosted by the tester in their own system and network in an isolated environment which doesn't cause any damage to any organisation or individuals.
This platform is known as Metasploitable.
In this blog, we can understand in detail the Metasploitable lab and how to use it...
Metasploitable
Introduction
Metasploitable is an intentionally vulnerable virtual machine designed to be exploited for testing and learning purposes. It is a popular tool for penetration testing and security research, providing a platform for practicing and improving hacking skills in a safe and controlled environment.
In this blog, we will take a detailed look at Metasploitable, including its features, how to set it up, and some of the most common exploits that can be used to attack it.
Features
Metasploitable is designed to simulate a real-world vulnerable system, with various services and configurations that can be exploited to gain access and perform attacks. Some of the features of Metasploitable include:
- Multiple services:
- Metasploitable includes a variety of services such as web servers, FTP servers, and databases, all of which can be exploited using different techniques.
- Realistic configurations:
- The system configurations in Metasploitable are designed to be realistic, including default passwords, vulnerable software versions, and insecure settings.
- Easy to set up:
- Metasploitable is easy to set up and run, with pre-installed software and configurations that require minimal configuration.
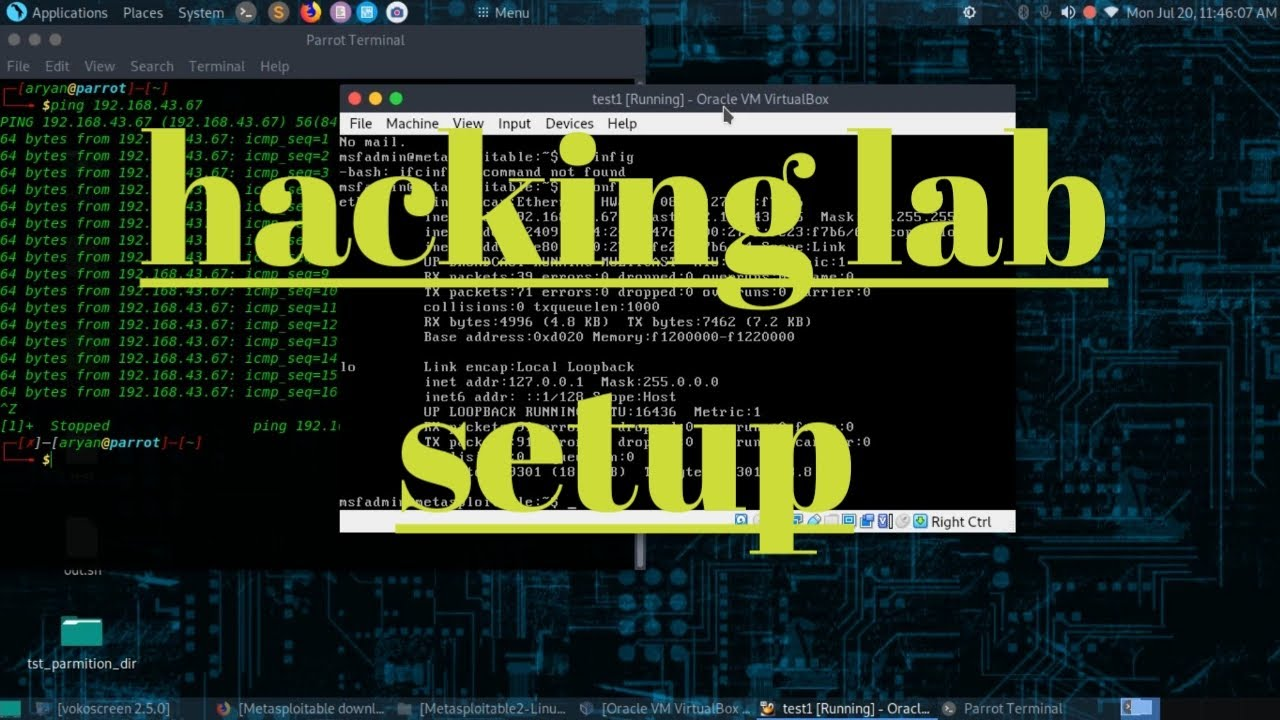
Setting up Metasploitable
To set up Metasploitable, you will need to download the virtual machine image from the official website and install it in virtualization software such as VirtualBox or VMware.
Here are the steps to set up Metasploitable:
- Download the Metasploitable virtual machine image from the official website.
- Install virtualization software such as VirtualBox or VMware on your computer.
- Open the virtualization software and create a new virtual machine.
- In the settings of the new virtual machine, select the option to use an existing virtual hard disk and choose the Metasploitable virtual machine image that you downloaded.
- Start the Metasploitable virtual machine and wait for it to boot up.
- Once the virtual machine is running, you can connect to it using SSH or a web browser, depending on the services that you want to access.
Common exploits for Metasploitable
There are many different exploits that can be used to attack Metasploitable, depending on the specific services and configurations that are running. Here are some of the most common exploits that can be used:
- Exploiting vulnerabilities in the Apache web server:
- Metasploitable includes a vulnerable version of the Apache web server that can be exploited using tools such as Metasploit to gain access to the system.
- Exploiting vulnerabilities in the SSH server:
- Metasploitable also includes a vulnerable version of the SSH server that can be exploited using tools such as Hydra or Metasploit to perform brute-force attacks on the login credentials.
- Exploiting vulnerabilities in the FTP server:
- The vulnerable version of the FTP server in Metasploitable can be exploited using tools such as Metasploit to gain access to the system.
- Exploiting vulnerabilities in the Samba server:
- Metasploitable includes a vulnerable version of the Samba server that can be exploited using tools such as Metasploit to gain access to the system.
Conclusion
Metasploitable is a powerful tool for penetration testing and security research, providing a realistic and controlled environment for practicing hacking skills. By setting up and attacking Metasploitable, security professionals and enthusiasts can gain valuable experience in identifying and exploiting vulnerabilities in real-world systems, and improve their overall security knowledge and skills. However, it's important to use Metasploitable responsibly and ethically, and only on systems that you have permission to test.